Internet Authentication Service (IAS) is the Remote Authentication Dial-in User Service (RADIUS) server in Windows Server 2003 family. As a RADIUS server, IAS performs centralized connection authentication, authorization, and accounting for many types of network access, including wireless and virtual private network (VPN) connections. As a RADIUS proxy, IAS forwards authentication and accounting messages to other RADIUS servers. A RADIUS client (typically an access server such as a dial-up server, VPN server, or wireless access point) sends user credentials and connection parameter information in the form of a RADIUS message to a RADIUS server. Microsoft Radius supports Windows 7, Windows XP SP2 and Mac OSX clients. This article provided an overview of Microsoft RADIUS and PEAP security and described how RADIUS security are implemented and deployed in IT infrastructure.
Prerequisite : Microsoft Active Directory, DNS, DHCP and Certificate Server, Cisco 1200 series wireless AP, MAC OSX 10.5, Windows XP Pro/Windows 7.
AAA Infrastructure:
Aunthentication: Microsoft Active Directory, Authorization: Microsoft Radius (IAS), Accounting: Microsoft Radius (IAS)
Security Measures: PEAP and Shared Secret
Encryption: MSCHAPv2
Configure IAS
Make sure all prerequisites mentioned above are ready and working. Install windows server and make it a member of Microsoft Active Directory domain.
Install machine certificate i.e. computer certificate in this server
Click on add/remove snap in
Click add
Select Certificates, click add
Check computer account radio button, click next
Select local computer, click finish
Right mouse click on personal and click on request certificate, follow screen shot
Click next, then click ok.
Install IAS as follows
Go to Add remove windows component, select internet Authentication Service, click ok.
Open IAS console from administrative tools, right click on IAS as above, click register service in Active Directory
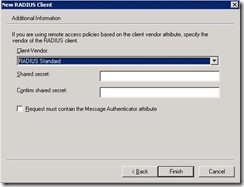
Add RADIUS Client, mention Cisco access point name and IP of Cisco Access Point, click next
Select Radius standard and provide shared secret and confirm, click finish. Shared secret must be same as you mentioned in Cisco wireless access point
Create Wireless access group in windows Active Directory and Add desired members in that group
go to administrative tools in IAS server, open IAS console, Add wireless access policy in Radius server
right click in wireless access policy and create new access policy
Select as above
Check Wireless and click next
Add wireless access group from active directory by click add button
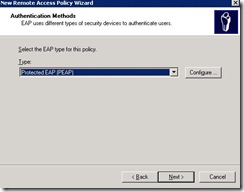
Select PEAP, click on configure
Click ok
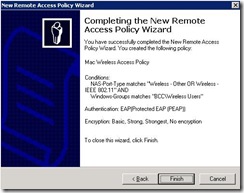
Click finish
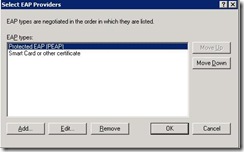
Now go to property of newly created access policy, click edit profile, click authentication tab, check EAP methods as follows.
Check encryption and authentication method. Use MSCHAP v2. Encryption 128 bits.
Configure Wireless access point as shown in the link
Now infrastructure is ready to authenticate iMac OSX 10.5, Windows 7 and XP via wireless.
Log on to an XP machine using user credentials who is a member of wireless access group. Go to run, type mmc and press ok. follow the steps mentioned above on top to install machine certificate but this time install user certificate i.e. check user account instead of computer account.
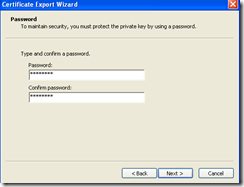
Once user certificate installed, right click on user certificate, click All task, click export follow screen shot
Save certificate in usb stick.
Configure Mac OSX 10.5
Now open iMac/Mac book pro. Go to utility, open Key Chain, select login, drag certificate from USB stick and drop it in key chain login, click ok
Type the password used while exporting certificate
go to system preference, open network, select AirPort, click on advance, click on +
Click on show all, select desired Mac wireless SSID, follow screen shot
type AD user name and password who is a member of wireless access group, select certificate, click add
Now authenticated as above. all done.
It is not necessary to bind Mac OSX 10.5 to AD to get wireless authentication via RADIUS. PEAP and certificate will do. now you can add user home drive, printer from print server.
On Windows XP or Windows 7 machine, log on using domain user credential who is a member wireless access group, install user certificate and machine/computer certificate as mentioned above. Turn on wireless, select SSID, click on connect, in few seconds it will be connected.































Hello, it really interesting, thanks
LikeLike
my pleasure 🙂
Raihan
LikeLike
No idea how to get a computer certificate for a MAC OS X computer? Looks like you authenticate the MAC access against a user credentials and not against the computer credentials.
LikeLike
I used PEAP, user cert and AD group to authenticate users. I reckon, computer cert will work only if you are a member of domain. In this case my iMac arent member of domain. You dont need to have computer cert in Mac. However, if you have XP and Win7 then I recommend installing user and machine cert. The method, I mentioned in my article also satisfy AAA procedure. So its secure. Do not add entire users in that wireless users group, add those who need it.
I hope, this would help you.
LikeLike
Hey!
I am new to mac and this is my problem!
I am running snow leopard on my mac. We are running WPA2 Enterprise wireless.
All of our current computers/notebooks are IBM, we join them to the domain.. give them dial-in rights and have a GP object that pushes out the wireless settings (including certificate).
I want to be able to get my MAC to get the same settings as is in the GP Object. I need to export a certificate I guess from our Domain Controller (also our Certificate Authority server). With that certificate I would imagine I would have to setup some sort of ‘keychain’ in order to get it to connect to the right SSID/VLAN on our wireless?
I really dont know, I am a microsoft man and I want to be converted!! Please help me, I would really appreciate it!
LikeLike
Unfortunately Mac OSX 10.5.8 or Snow Leopard does not work with Microsoft GPO, User Profile and MS AD log on script. So it will not syncronise with GPO. Keychain store security object like password, certificate etc. user must log on to XP/Windows7 machine, get certificate and export it to keychain. Alternatively, export user certificate from CA Authority to KeyChain. You dont need to setup anything to get certificate in keychain. Export certificate in a USB stick, then plug in to Mac, drag and drop it to keychain. It will prompt for local password. Provide local password and you are in. Cisco AP and Mac client must be in same VLAN in order to talk to each other. Select right SSID and provide Domain credentials, select certificate and connect.
Rest I believe I mentioned in that posting if you are using IAS and Mac client. You dont need to convert mate if you dont want to. If you still stuck then get back to me. Regards, Raihan
LikeLike
Pingback: Step by Step guide to build a Cisco wireless infrastructure using Cisco WLC 5500, Cisco 1142 AP and Microsoft Radius server « Information Technology Blog
p
LikeLike
How can i configure LAN to send and receive email without connecting to Internet?
Abraham Bright
LikeLike
I have tasked to set up cisco airnet 1131ag k devices to enable access to resources on windows 2008 R2 server if they have AD account or as guest. After some research I understand that I need to set up the radius sever-
I have done this and followed your instructions and further configured the WAP device using the Cisco notes, I am not getting client authentication.
I am not sure how to troubleshoot the issue. How do I check the Cisco router is it is receiving requests from laptop etc?
I have seen CLI instructions, where do I enter them?
appreciate your assistance
ifty
LikeLike
Authentication failure may result from not configuring AD Property of the user.
Open AD users and Groups>Select user>Property>Remote Access>Allow through remote access policy>Apply.
Create an AD Group, Add Users into the group and Add that group into Radius Server. you will be authenticated
LikeLike
my problem is i’ve set up wireless using 802.1x so wireless users authenticate to the RADIUS server. users using computers on the domain can access the network through the wireless access points but computers that are not on the domain cannot even though a domain account is entered. mobile devices can also
LikeLike
In the nondomain computer and iPhone you need to import certificate before they can access.
LikeLike