The virtual private network (VPN) technology allows users working outside the office premises connect to their private network in a cost-effective and secure way. Creating this type of internetwork is call virtual private networking. VPN uses ordinary internet as a medium to reach end point i.e. private network or inside corporate network.
In a VPN connection, data is encapsulated or wrapped up and encrypted with a header that provides routing information allowing it to traverse the shared or public transit internetwork to reach its destination. The portion of the connection in which the private data is encapsulated is known as the tunnel. VPN connections use either Point-to-Point Tunnelling Protocol (PPTP) or Layer Two Tunnelling Protocol/Internet Protocol security (L2TP/IPSec) over internet as medium.
Figure: A typical VPN connection, source Microsoft Corp.
So what is required to deploy VPN in an organisation. A systems administrator can accomplish VPN if he/she has the following components in place.
VPN Server (Windows 2008/2003)
Internet infrastructure with Public IP
VPN Clients (Windows 7, Windows XP or Mac OSX 10.5.x)
Intranet infrastructure (Microsoft networks, AD, DNS and DHCP with enough IP available)
Certificate infrastructure (Microsoft AD CS)
Authentication, authorization and accounting (AAA) infrastructure (Windows/Radius)
Deployment: you can install Windows server 2008 in a standard hardware with two NICs. In my situation, I used three NICs as my VPN server is also wireless authentication server. So, it works both for me (VPN+Wireless). One NIC for internal network, another for public IP (VPN) and another for wireless networks (ignore third NIC if you are not in same situation). All NICs must have static IP. You have to pipe through public IP to your VPN server. VPN server must be a domain member and computer/machine certificate installed in VPN server. I configure DHCP in VPN server. So that VPN client can obtain IP from this server not from internal DHCP server. It makes my life easy and got enough IP. You can mention existing DHCP server also while configuring VPN if you choose not to configure DHCP in VPN server. Here, I will explain about L2TP IPSec deployment. L2TP IPSec is secure and preferred VPN for me. The following screen shots will do the rest for you.
Here, you can select VPN+NAT, that will do.
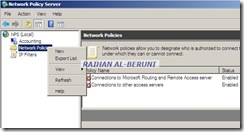
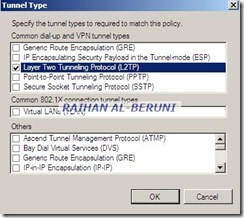
Here, you have to select tunnel type, Encryption method, NASPort Type. It’s highly important.
I used Microsoft server 2008 R2 as VPN server using L2TP IPSec. I used windows authentication not Radius. In this case, the secure connection appears to the user as a private network communication, however this VPN connects over a public networks. An user and a machine certificate are required to connect to VPN server. Also user must be a domain user. In your situation would certainly be different. Do as appropriate in your situation. I hope this would help you to configure VPN server.

![clip_image001[4] clip_image001[4]](https://araihan.files.wordpress.com/2009/10/clip_image0014_thumb.gif?w=244&h=123)

































Hello my name is Anthon, I really liked your article! Nice work
LikeLike
Thanks for visiting my site. Raihan
LikeLike
Really nice job dude. Thanks a lot.
Raj
LikeLike
Hi mate,
Any chance you could provide a printer friendly version? The images are really compressed and when printing the quality is pretty bad and you can’t read anything.
thanks,
Hamid
LikeLike
print it as pdf. if you dont see clear click on picture.
LikeLike
hello, great article, do you know, as you’look good on ipsec, if windows 2008R2 can do a ipsec tunel with a cisco ASA on the other side ?
LikeLike
Please explain your design, what you configuring uisng ASA and IPsec. Here are some readings for you.
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00807213a7.shtml
http://www.cisco.com/en/US/docs/security/asa/asa80/configuration/guide/l2tp_ips.html
LikeLike
in fact I’ve 2 lan, on in my company with a asa FW, and one hosted with a 2008 R2 running live on the internet. on this 2008R2, I’d like to run hyperV VM, but I’d like these CM to have private IP behing the public IP of the hosted server, and this hosted server connected to IPSEC to my asa… not sure it’s clear…
LikeLike
Hi,
It is great article. I am new in system administration. I am planning to setup IPSec VPN in my two proxy server which are running in Window 2008 server R2. I have 50 mobile phone which are running window mobile 6.5 to tunnel in to the VPN and i am using NCP Secure Entry client. Kindly advise if i need to do some additional thing out of the step you have explained in the article ?
Thank you very much.
Regards,
Handoko
LikeLike
I am certain that windows mobile will work with Microsoft VPN and steps are mentioned above. No further steps necessary if you are completely using windows. But for NCP you need to check with them.
LikeLike
Hi Raihan,
another question, which ports number that i need to open ?
basically i plan to install VPN server and proxy server together in one server (window 2008 server R2).
could it be done ?
Kindly advise
Many Thanks inadvance
LikeLike
When you configure VPN server, you have to create a policy to allow L2TP IPSec protocol from external to internal network. You dont need to create custom protocol in TMG. Expand All protocol and you will see L2TP IPSec.
LikeLike
Hi Raihan,
First, I just want to tell you that I really like your article.
I Just have one question. At the end of your article you mentioned that a person would need a computer and user certificate to be able to connect to the VPN server. Why do you need a user certificate? Isn’t enough with the computer certificate only?
Thanks for your information.
LikeLike
It depends on your configuration and security objectives. Computer and Users certificates are my prefered way of doing it. This article is sample guidance, feel free to change your own config.
LikeLike
Hi Raihan,
Thanks for your reply.
But for me it’s not clear one thing yet.On the client side(Windows 7 in my case) how do you setup the connection with both certificates computer and user?, Where’s that setting when the vpn connection is being setup?
Thanls again for the info.
LikeLike
I followed your instructions but it does not work. What about IPSec preshared key (as I do not want to use certificates?) Where do you configure it? I tried to right click on RRAS and type my key there but it did not help? Is there a place to configure it in policies
LikeLike
As the article title say, this is L2TP IPSec so you need certificate. However you can use Preshared Key. http://support.microsoft.com/kb/240262
and http://support.microsoft.com/kb/281555
you need to create policy with preshared key. why not configure a CA in your DC and do L2TP IPsec. certificate is more secure than presshared key.
LikeLike
Im actually trying to do the reverse, our VPN appliance was fried in a remote office and as a temporary workaround, i’m trying to have the remote 2008 server dial OUT via L2TP but it just hangs and reports error 789, but when i look at netstat it seems the server never even attempts to dial out. Is there a setting , rule or reg hack I need to do to allow the 2008 r2 server to dial OUT using l2tp?
LikeLike
Please use this http://microsoftguru.com.au/2010/08/24/how-to-configure-site-to-site-vpn-using-forefront-tmg-2010/
LikeLike
hi there,
any chance of uploading the network diagram including the sample IP addressing please.
thank you in advance.
erwin
LikeLike
This article really helped me with my assignment while giving me a great work-related information. I made sure to cite your work. Thank you very much.
LikeLike
Dear Raihan,
very nice article, but I have a problem with the following scenario:
I have Hyper V Host running a Virtual Machine with Server 2008R2 configured as RRAS and Radius Server and a Wireless AP configured to use Radius for authentication. My problem is now that the Radius protocall is not reached at the service. I think the main problem is that the virtual network card and network seems to be a egde traversal link. When I disable RRAS and configure only NPS the connection works. When I configure RRAS without “Enable Security on selected …” and allow edged traversal in the advanced firewall for the radius ports it works also. But when I select “Enable Security on selected…” it doesn´t.
Did you know where I can configure the static filtering to allow this?
Best regards
Christian
LikeLike
I reckon, vNetwork configuration was right or something miss-configured in your Hyperv. Win2k8 L2tp VPn works straight fordward once you configure whether virtual or physical. its the communication between your physical switch and virtual switch might be going wrong.
LikeLike
Question: Which software do you use on the client side to connect to the VPN once you have done the steps you kindly published here.
Many Thanks,
Agustín.
LikeLike
you have to configure VPN dialer http://microsoftguru.com.au/2009/10/15/windows-7-l2tp-ipsec-vpn-dialler/
LikeLike
hi!
I have a single NIC and two public IPs. I’ve setup the VPN to connect successfully. But the client can only access the server, loses access to the internet. I need the client to be able access internet via server’s internet. Is it a possible scenario with only one NIC?
Thanks,
LikeLike
Do you have any firewall or proxy in place? if so please publish policy to provide access to internet.
LikeLike
Raihan Al beruni need you help i am getting Error code 800
please respone
LikeLike
Hi, Raihan. Good job men. Can DDNS be implemented instead of public IP ?
LikeLike
Thanks for the helpful article, however, got few questions.
1)For L2tp, do I need to purchase a certificate from a vendor?
2)Can I use this to connect mobile phones
3)Is this for R2 or does the server 2008 standard edition support this?
LikeLike
I have two private IP’s to access the internet through ISA Server but when try to configure external private IP on ASA cannot access the Internet.can you help me in this regard where I am mistaking please.
LikeLike
Hi, nice work and excellent topic …!
I have a question regarding NIC cards
Can I use one NIC card since I’m planning to have my VPN server sits behind my firewall and will only open the necessary VPN ports on the firewall then forward all VPN trafic on the firewall to the VPN server
So the public IP will be on the firewall and the VPN server will have a local NAT IP
Thank you
LikeLike
Yes you can have a L2TP IPsec server in your internal network as long as you forward all necessary ports.
LikeLike
Hello Raihan, Great article. It helped me a little to understand part of the job I need to be done. This will do fine for client->server connections. Any tips on how can I setup a lan to lan vpn between two offices, and test it? Thanks in advance.
LikeLike
Best way to achieve site to site VPN using Forefront TMG. You can use PPTP VPN between two sites but this will not achieve great result if you are bandwidth hungry and wants to do QoS. Best option is Cisco Router.
LikeLike
hi i need to need to secure rdp connections for a workstation in my workplace,we are using windows server 2008 as server os and windows 7 as client.i need to get secure rdp connections when i tried to get connected to my workstation,when i am outside my network…….does configuring l2tp into server solves my problem
LikeLike
Yes. you can use L2TP IPSec with certificates.
LikeLike
Use Microsoft RDS instead of L2TP VPN
LikeLike
Good Morning Raihan ..
I have a small problem with a VPN L2TP enabled only with the option of pre-shared key ..
The stage is so …
2 W2K8 R2 domain controller Standard
1 member running W2K8 R2 Standard Server with Forefront TMG Management Gateway 2010, this team has two network cards .. One for the LAN and one for WAN (my ISP gives me a dynamic IP issues and set up via a router doing NAT WAN card to the network, ADSL)
In the ServidorTMG I have both PPTP and L2TP PPTP options enabled … everything works smoothly, but with pre-shared key l2tp and fails to connect.
I have indicated on the NPS server a policy that has the following options to grant access ..
Access Permission: Grant
Authentication Method: MS-CHAP v2
framed prococol: PPP
Service-Type: Framed
Policy Encryption: Enabled
Encryption: 40bit, 56 and 128
I saw here in your own blog, you have other options enabled in your policy to grant access, but these are certified to handle ..
I must enable these options, although not this autenticcando through certificates?
NPS is absolutely necessary to manage the policy to grant access?
Serious enough that only the TMG will validate the cf options to grant full access?
Beforehand thank you very much…
LikeLike
I am not clear about your question? What is your concern/question?
LikeLike