Step1: Prepare AAA Environment
- Windows Server 2008 SP2 or Windows Server 2008 R2
- Active Directory Domain Services
- Active Directory Certificate Services
- DHCP
- Radius i.e. NPS must be a member of domain
- Computer certificate installed in Radius Server
- Windows 7, Windows XP or Mac OSX 10.5.8 Client
- Cisco Wireless Access Point
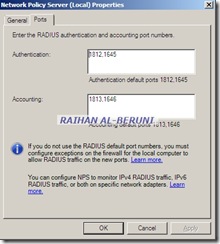
Step2: Installation
Start menu>Administrative Tools>Server manager>Roles>Add Roles
Step3: Setup Clients
Administrative Tools>Network Policy Server>Radius Client>Right Click>New Radius Client
Radius Secret mentioned here must be same in Cisco Wireless Access Point. You must verify connection by clicking verify.
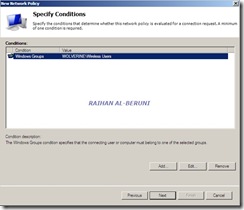
Step4: Setup Policy
Network Policy Server>Policies>network Policies>Right Click>New
This is highly important part of entire config. Based on your need, you have to choose desire config type among all.
VPN Tunnel Type:L2TP
NASPort Type: VPN or Wireless
EAP Type: EAP-TLS, MSChap v2 or PEAP
AD Group: Wireless User Group or VPN User Group
Here, you can choose one or both depending on your infrastructure. I have shown both VPN and Wireless Client.
Here, I am showing both EAP type for this article. But you have to choose only one again depending on your infrastructure.
Smart card or Certificate is the best option. For Windows 7 and XP, only certificates will work smooth as silk. However, if you have Macintosh Client then you have choose Certificate and PEAP.
If you want VPN client to authenticate via Radius i.e. NPS then select Tunnel type.
Here, I explained standard Radius config. I would recommend following for two different situations:
- L2TP, Certificate and EAP for VPN Client
- Certificate, PEAP and MSChap v2 for Wireless Client.
You can have more then one policy in NPS. A single server can be used to authenticate both VPN and Wireless Client. For some weird reason, my Macintosh client did not work with only user and machine certificate. Apple support advised me to use user cert and Radius shared secret instead. But for Windows 7 and XP client, certificates and EAP will work smooth as silk.
Further Help:
Keywords: L2TP, Radius, NPS, Windows Server 2008, Certificates





































Pingback: Step by Step guide to build a Cisco wireless infrastructure using Cisco WLC 5500, Cisco 1142 AP and Microsoft Radius server « Information Technology Blog
Dear Raihan,
I was able to establish L2TP for XP and 7 clients within the domain. And I tried user cert and Radius secret as you suggested in this article but of no avail.
So I have two questions
1. How do get my MAC client connected to the L2TP VPN?
2. How do I get the clients from outside the domain to connect to the VPN. Like for example if I want to connect from home to my L2TP server at work how would I go about it? Is there a way forward?
Do I need to export certificates to my home machine? If yes how would I do it?
If not what is the best method for this?
Your help on this occassion is gratefully received.
Thanks
AR
LikeLike
Hello AR,
I tried on iMac to connect Microsoft L2TP VPN but it does not work. This is due to compatiblity issues with Microsoft and Apple. Alternatve option for iMac to use Microsoft Radius authentication.
From you home, you will not be able to connect L2TP server even if you import certificate. But Radius will work because radius checks AD username and password and computer certificate.
See more http://microsoftguru.com.au/2009/08/17/microsoft-radius-server-ias-apple-imacmacbook-pro-osx-10-5-and-xp-pro-step-by-step/
LikeLike
Hi Raihan,
Many thanks for replying to my email. but I forgot to mention that my L2TP VPN server is windows server 2008 R2 and the instructions you have sent are for Windows 2003. Also the instructions are for Wireless VPN from MAC, but I would need instructions for Wired VPN as well.
I wonder if you have done this before?
Thanks
Abdul
LikeLike
I have configured WLC2100 and Windows 2008. The server only authenticates Domain PCs, doesnt authenticate any other PCs although prompting for username and password.
LikeLike
what tunnel type you selected? L2TP authentication must be domain PC. you can configure PPTP with user or group authentication.
LikeLike
Will this work if the NPS box is only acting as a DHCP relay agent and not DHCP?
LikeLike
Please clarify more. NPS and DHCP are the roles in Win2k8. you can install more then one roles in win2k8.
LikeLike
How we can test if this configuration work on the client
LikeLike
Create infrastructure, Configure as it says and test it.
well I tested myself and it works.
LikeLike
If I want certain guest accounts created just for wifi access and authenticating to the RADIUS and the machine they are using is not a member of AD, can you tell me best suitable setup in this regards? Domain users / computers will also be connecting and authenticating for wireless purpose. Thanks.
LikeLike
Create a standard AD user account and password for guest users and follow http://microsoftguru.com.au/2009/08/17/microsoft-radius-server-ias-apple-imacmacbook-pro-osx-10-5-and-xp-pro-step-by-step/
LikeLike
RADIUS server 192.168.xxx.xxx:1812,1813 is being marked alive.
4 Jul 8 20:22:02 Warning RADIUS server 192.168.xxx.xxx:1812,1813 is not responding.
I am getting the above error with Cisco 881W acces points (using CISCO 881W-GN-A-K9 router with wireless), it was working and suddenly stopped. I do have few Linksys / Cisco WAP4410N accespoints which are working fine. My NPS is running on a Windows 2008 R2 domain controller.
LikeLike
This is not a best practice at all. Please use separate server for NPS and try again.
LikeLike
Thanks for update.
I am in the process of doing the same. It is stopped suddenly,any chance know what is the reason for above error.
LikeLike
WOW Raihan Al-Beruni ,Brother You are the man of IT, you know I did 27 certification andh have above 12 years exprince but I never saw IT guy like you, I realy want to see that who is that nice guy who,s put every things step by step, I love it bro and God bless you, Thanks
Best Regards
Arshad
LikeLike
thanks for visiting my site.
LikeLike
i have read your soluation but i have question does client laptop required to joing to domain to be authenticated with radius.
LikeLike
yes they need to be a domain member. But if they are not than you have to export certificates to standalone machine and use a domain account to join network.
LikeLike
i have test that but one problem even i didnt select validate certificate am able to login to wireless ,,, i think it must check the certificate if not valide it should not let me login by the even though am able to login.
LikeLike
i have export the certificate from nps server and import it in client laptop non domain to trust root authority ,and i have configure it to validate the certificate but am able to login the wireless network with checking the certificate. kindly correct me if am wrong regarding the steps to configurate the client machine am using 802.1x
LikeLike
Is it working without domain control in client pc
LikeLike
please explain your questions
LikeLike
regarding ca certificate for nps server , how to prepare this request coz it is showing in configuration server name of ca only no nps server name
LikeLike
in this certificate option what kind of certificate shall i request
domain controller authentication or domain controller
LikeLike
please explain your questions? Use enterprise root CA or standalone CA
LikeLike
Will it work for computers out side domain, like guest or non company laptos, how can we connect laptops with out joining to domain
LikeLike
Hi Raihan,
Thaks for the posting such a nice KB.Just wanted to ask one thing abot you above example.You have use ip of 10.10.10.15.this Ip belongs to WLC/APs or your Domain controller.Could you please tell me in detail asi am i am new in NAP
LikeLike
What do you know about setting up NPS and using MAC address authentication? We are not having any luck here with this type of setup!!
LikeLike
Understanding exactly what people want, you prepare it perfectly. Nice…..
LikeLike
How can I change the network domain in the NPS role.
LikeLike