Placing a firewall in a corporate network puts you in commanding position to protect your organisation’s interest from intruder. Firewall also helps you to publish contents or share infrastructure or share data securely with eternal entity such as roaming client, business partners and suppliers. Simply, you can share internal contents without compromise security. For example, publishing Exchange Client Access Server, OCS 2007 and SharePoint front-end server in the perimeter.
More elaborately, the front-end and the back-end topology is commonly seen in multi-tier applications where the user interacts with a front-end server (Example: CAS server) and that server interacts with a back-end Server (Example: HT server). In this exchange deployment scenario, users interact with a front-end CAS Web server placed in DMZ or perimeter to get Outlook Web Access for reading and sending email. That Web server must interact with the back-end mail server or HT server, but Internet users do not need to interact directly with the back-End HT server. The front-end and back-end server(s) does all these for you providing maximum security. visit Exchange 2010 deployment in different firewall scenario
In this article, I am going to illustrate Back-to-Back Firewall with DMZ. This topology adds content publishing to the back-to-back perimeter topology. By adding content publishing, sites and content that are developed inside the corporate network can be published to the server farm that is located in the perimeter network.
Advantages
- Isolates customer-facing and partner-facing content to a separate perimeter network.
- Content publishing can be automated.
- If content in the perimeter network is compromised or corrupted as a result of Internet access, the integrity of the content in the corporate network is retained.
Disadvantages
- Requires more hardware to maintain two separate farms.
- Data overhead is greater. Content is maintained and coordinated in two different farms and networks.
- Changes to content in the perimeter network are not reflected in the corporate network. Consequently, content publishing to the perimeter domain is not a workable choice for extranet sites that are collaborative.
Assumptions:
- Internal IP range: 10.10.10.0/24
- Perimeter IP Range: 192.168.100.0/24
- Public IP:203.17.x.x/24
Note: In the production environment, perimeter IP must be public IP accessible from internet.
| Computer | Internal NIC Configuration | External NIC Configuration |
| Back-End TMG 2010 (two NICs) |
IP: 10.10.10.2 Mask:255.255.255.0 DG:Null DNS:10.10.10.5 |
IP:192.168.100.4 Mask:255.255.255.0 DG:192.168.100.5 DNS:Null |
| Front-End TMG 2010 (Two NICs) |
IP:192.168.100.5 Mask:255.255.255.0 DG:null DNS:10.10.10.5 2nd DNS:203.17.x.x (public IP) |
IP:203.17.x.x (public IP) Mask:255.255.255.0 DG:203.17.x.1 (public DG) DNS:203.17.x.x (public DNS) |
| DC | IP:10.10.10.5 Mask:255.255.255.0 DG:10.10.10.2 DNS:10.10.10.5 |
Not Applicable |
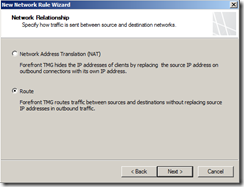
Routing Relation:
| Back-end TMG | Internal to PerimeterPerimeter to External
Perimeter to Internal |
RouteNAT (Default)
Route |
| Front-End TMG | Internal to External (All TMG Default) |
NAT (Default) |
Persistent Routing in Front-End TMG and all servers placed in perimeter/DMZ: You must add following routing table in front-end TMG server and all other servers placed in perimeter in elevated command prompt. To do that, just log on as administrator, open command prompt and type following and hit enter.
Route ADD –P 10.10.10.0 MASK 255.255.255.0 192.168.100.4
Configure Back-End TMG Server:
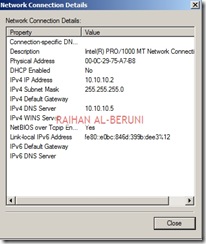
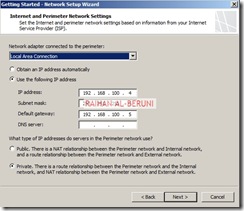
Log on to TMG Server using Administrative credentials and define internal IP as shown on TCP/IP property.
Define Perimeter IP As shown on TCP/IP property
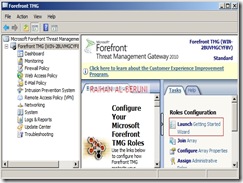
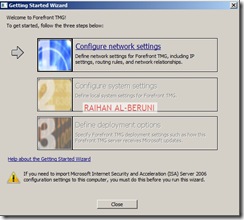
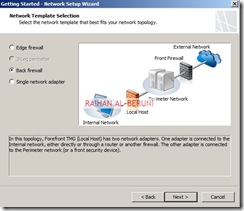
Now add TMG server as a domain member. Install Forefront TMG using Step by Step Guide Lines. Open TMG Management console, Launch Getting started Wizard. Configure network Settings. Select back Firewall.
Click Configure Systems Settings.
Click Define Deployment Options.
Click Close. Apply Changes and Click Ok.
Create connectivity with AD and DNS.
Add and Verify IP addresses of internal (10.10.10.0/24) and perimeter network (192.168.100.0/24).
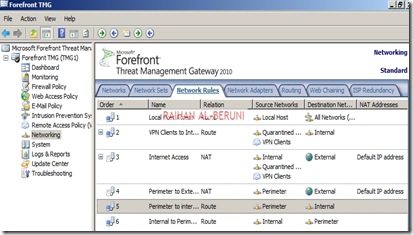
Add Network Rules:
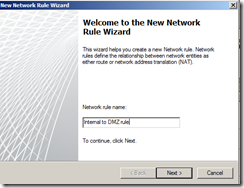
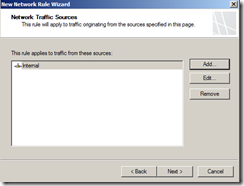
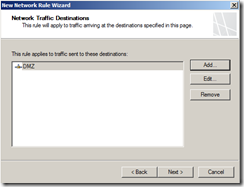
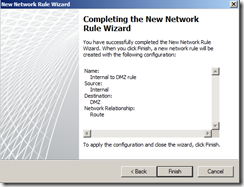
Create Network Rule. To do that click on Networking>Network Rules>Create a New Network Rule Wizard.
Here, Rules 1 to 4 will created by default while initial configuration as shown below. You have to create rule 5 and 6 by repeating above steps.
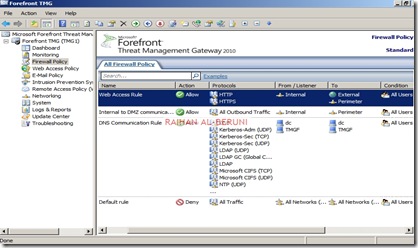
Configure Firewall Rules:
| Actions | Allow |
| Protocols | DNS, Kerberos-Sec(TCP), Kerberos-Sec (UDP),Kerberos-Admin (UDP), LDAP, LDAP (UDP), LDAP (Global catalog), Microsoft CIFS (TCP) ,Microsoft CIFS (UDP), NTP (UDP), PING, RPC (All Interface) |
| Source | DC, Front-End TMG |
| Destination | DC, Front-End TMG |
| Conditions | All Users |
Now Publish DNS for perimeter network. Right Click on Firewall Policy, Click New, Click Access Policy, Name new access policy. On the selected protocol add DNS, Kerberos-Sec(TCP), Kerberos-Sec (UDP),Kerberos-Admin (UDP), LDAP, LDAP (UDP), LDAP (Global catalog), Microsoft CIFS (TCP) ,Microsoft CIFS (UDP), NTP (UDP), PING, RPC (All Interface), Click next.
On the Access Rules Sources, Click Add, Select Computers, Click New, Type Netbios name of DC and Type IP, Click Ok. Select DC and Click Add. Repeat this process for Front-End TMG server i.e. add name and IP of front-end TMG server and Click Add.
On the Access Rule Destinations, Click Add, from the computers list add DC and front-End TMG servers. Click Next and Click Finish. Apply changes and click ok.
Create an Access Rule allowing all outbound traffic to go from internal to perimeter.
| Actions | Allow |
| Protocols | All Outbound Traffic |
| Source | Internal |
| Destination | Perimeter |
| Conditions | All Users |
Create another access rule allowing HTTP and HTTPS to go from internal to perimeter and external.
| Actions | Allow |
| Protocols | HTTP, HTTPS |
| Source | Internal |
| Destination | External |
| Conditions | All Users |
Configure Front-End Forefront TMG Server:
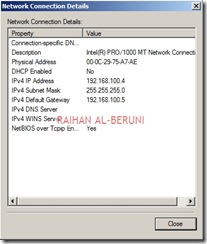
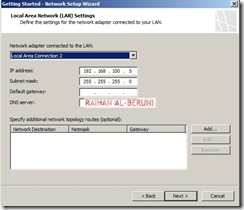
Prepare another Windows Server 2008 x64 computer. Log on as an administrator. Define internal and external IP addresses as shown below.
Internal TCP/IP property:
External TCP/IP property
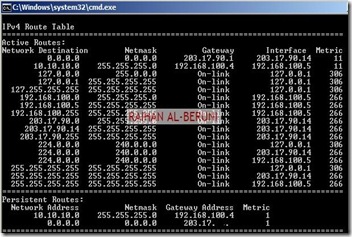
Open Command prompt>type following command to add persistent Routing:
c:\>Route Add –P DestinationIP DestinationMask SourceIP
c:\>Route Print
Add Front-End TMG as domain member. Follow same installation and initial configuration options shown in back-end TMG server. There are only two differences while initial Network Settings configuration that are selecting internal (192.168.100.0/24) and external (203.17.x.x/24) network. Those are shown below.
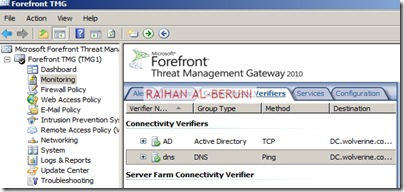
Create Connectivity Verifier with AD, DNS and Web.
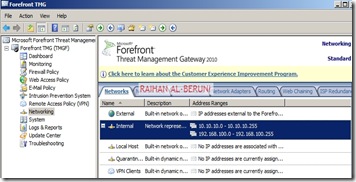
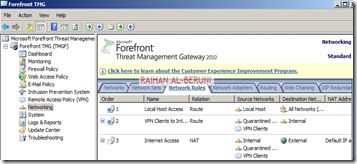
Networking>networks>internal>Add 10.10.10.0/24 and 192.168.100.0/24 as internal IP. Make sure internal IP and perimeter IP of back-end server are both internal IP of Front-end server. keep default routing rules in Front-End TMG. Configure property of internal network.
Verify Network Rules:
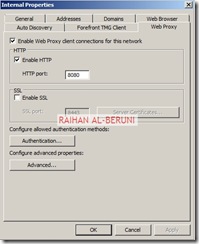
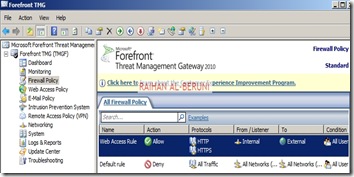
Configure firewall to allow HTTP/HTTPS : Firewall Policy>New>Access policy>Allow HTTP and HTTPS for all users. Do not Allow all outbound traffic to go from internal to external in Front-End Server. Only specific ports and protocols should be allowed.
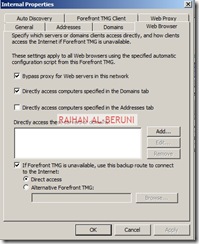
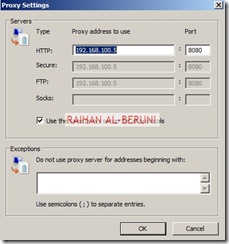
Test Firewall: Log on to a computer in internal network behind Back-End Firewall. Setup Proxy in IE as shown below and browse internet.
Placing Front-End Server(s) or a member server in DMZ:
One you have completed above steps, you are ready to place any Front-End server(s) such as Exchange CAS, OCS 2007 and SharePoint Servers in DMZ/Perimeter. You need to import certificates from Enterprise Root CA placed in internal network (behind Back-End TMG) to Front-End TMG server to publish secure web sites such as OWA, Outlook Anywhere or OCS. All Publishing Rules Applied in Front-End TMG server. Here, I am not writing OWA or Anywhere because it would redundant for me to write again as I have shown all these in my previous posting. Visit the links mentioned below.
Prerequisite for placing a member server in DMZ: A member server must have following TCP/IP configuration to work in perimeter.
| IP | 192.168.100.0/24 (Perimeter IP Range) |
| DG | 192.168.100.5 (Internal IP of Front-END TMG server) |
| DNS | 10.10.10.5 (Internal DNS) |
| 2nd DNS | 203.17.x.x (Public DNS) |
| Routing | As Mentioned in Persistent Routing Section of this Blog |
Relevant Articles:
Forefront TMG 2010: Publish Outlook Web Access and Exchange Servers using Forefront TMG 2010
How to publish Exchange Anywhere in Forefront TMG 2010
How to publish Exchange ActiveSync in Forefront TMG 2010
Exchange 2010 deployment in different firewall scenario
Forefront TMG 2010: How to install and configure Forefront TMG 2010 —-Step by step
How to create E-Mail protection Policy in Forefront TMG 2010
Forefront TMG 2010: Publishing Exchange server 2010


























Hi Raihan
This is Khaja, i am new to windows administration and i want to install TMG2010 i don’t know about TMG can you tell me why we use TMG and what the basic configurations and installations i need to do in my machine. Plese reply me back.
LikeLike
Hello Khaja,
Forefront TMG is the upgrade version of ISA 2006. I reckon, you need to read http://technet.microsoft.com/en-au/evalcenter/ee423778.aspx
TMG can be used as a proxy, proxy cache, reverse proxy, firewall, gateway, content filter, VPN, web publishing so on and so forth.
Regards,
Raihan
LikeLike
Pingback: How to configure reverse proxy using Forefront TMG 2010— step by step | MicrosoftGURU
Hi, lovely document I have has a read through as I am tryijng to configure TMG server as a back firewall but behind an ASA, do you have any documentation or guides on how to do this that I could read?
Many thanks.
LikeLike
Hi Steve, I dont have any specific guide for your situation however this link might be helpful for ASA http://www.cisco.com/en/US/docs/security/asa/asa72/asdm52/user/guide/getstart.html and http://www.cisco.com/en/US/docs/solutions/Enterprise/Borderless_Networks/Smart_Business_Architecture/SBA_Enterprise_BN_Internet_Edge_Configuration_Guide_H2CY10.pdf
For back end TMG config, use back-end config part of my blog. Hope that help. Raihan
LikeLike
Pingback: How to configure Forefront TMG 2010 as WPAD server (Auto Proxy Discovery)—Step by Step | MicrosoftGURU
Helpful blog, bookmarked the website with hopes to read more!
LikeLike
I still don’t seem to get the routing …
I have a regular Time Warner gateway.
I am only setting up a backend TMG
Backend TMG- Network …
{External} IP: 10.1.1.254 / 24 | GW 10.1.1.1 |DNS:null (can IP ping outside world)
{Internal} IP: 10.7.7.1 /24 |GW null | DNS 10.7.7.11 (AD DNS) (can ping inside world)
Internal Network —
IP:10.7.7.0 (dns .11) |GW 10.7.7.1 | DNS:10.7.7.11
so is it route 10.7.7.0 mask 255.255.255.0 10.1.1.254 ????
and if so, shouldn’t I be able to ping the external gateway from the internal network?
I want to have all these settings correct before I install.
Thanks – S
LikeLike
Hello Sean,
No not at all. TMG block everything by default. you need to open/allow in firewall policy to ping external gateway. Probably, you are trying to configure edge firewall and configured backend firewall. Is your gateway acting as a front end firewall then TMG can act as backend firewall otherwise your description shows that you need to configure edge firewall. Please explain a bit more if I didnt understand your network design.
Raihan
LikeLike
Actually – I guess what I really am seeking is the correct route add -p command.
I know that the Internal network – 10.7.7.0 mask 255.255.255.0
What I am not sure of, is do I complete that with the Back End Firewall External address — 10.1.1.254 or do I select the Front Firewall of 10.1.1.1 address.
So does the command look like:
1. route add -p 10.7.7.0 mask 255.255.255.0 10.1.1.254
or
2. route add -p 10.7.7.0 mask 255.255.255.0 10.1.1.1
Thanks S
LikeLike
Once you install TMG and select a topology. routing will be automatically selected by TMG unless you have special routing need. You did not need answer my question, to help you and provide correct answer…….. Your router is working as Front end firewall or not? If yes then you need to add routing table in backend server otherwise you donot need to use route add command.
LikeLike
Im trying to foncigure the TMG Server but im getting an error on the network configuraction i di it jest like u did, and go there is no such objet on the server>
why:?
We have a checkpoint on front and isa 2006 on back, we are trying to upgrade to TMG.
LikeLike
First you follow this http://microsoftguru.com.au/2010/03/08/forefront-tmg-2010-how-to-install-and-configure-forefront-tmg-2010-step-by-step/ in your test environment to learn correct installation than you try back to back firewall.
LikeLike
Pingback: FF TMG 2010: Configure ISP Redundancy— Step by Step | MicrosoftGURU
I am going to be using this setup at home using virtual machines. I want this type of DMZ with a front end TMG and a backend TMG.
The problem is:
Does this setup assume you have a Cisco router and not a “Linksys WRT 160N” (like I have at home)? Would I have to find a device where I could turn off Nat?
LikeLike
TMG does not see what type (manufacturer) of device place in front. you can configure NAT separately or turn off or create custom rules.
LikeLike
I want to use this type of setup since I am in IT and want to set it up at home and use it for years, so it becomes second nature to me and if any future companies I work for needs a back to back TMG, I’ll already know how to set it up and administer it.
LikeLike
You know what. I just thought about this. Couldn’t I just remove the “Linksys WRT 160N” and connect directly to the modem?
LikeLike
I am not clear about this question. please explain a bit.
LikeLike
What would you do if you had the following device:
http://www.linksysbycisco.com/UK/en/products/WRT160N
Would you leave the device alone and accept the default setting (which is NAT)?
Would you make any adjustments on it before placing a back-to-back firewall (AKA: TMG) behind it?
LikeLike
What I am saying is:
The firewall on this Linksys WRT160N blocks all ports. Period.
Would you turn off the Firewall portion “off” and let DHCP (on the Linksys WRT160) hand out static IP’s to the front end TMG and backend TMG?
If it was your device, how would you configure it with a back-t0-back TMG firewall solution?
LikeLike
DHCP does not hand out static IP DHCP is dynamic. TMG is an awesome technology. I would utilize TMG as much as I can. So Turn off NAT or firewall on this device and let TMG manage everything.
TMG must have static IP in all NIC whether front end or back end. TMG got many features like web proxy, firewall, reverse proxy, proxy cache, content filter, many more.
LikeLike
I’ll hand out the static ip addresses (via DHCP) – using the MAC addresses of the two TMG servers.
LikeLike
Hi Raihan, very nice articles here.
I have to setup a TMG server as a reverse proxy into a DMZ to use it to publish Lync and Exchange sites. I have a fortigate as front firewall.
Is the back firewall the best choice for my setup? If yes wich rules do I have to create into my TMG back firewall (reverse-proyx)?
Your help is very appreciated
Regards,
Bruno
LikeLike
As you already have a Front Firewall than TMG will be in back firewall config. Use web publishing rule to publish any websites in TMG. http://microsoftguru.com.au/2010/08/08/how-to-configure-reverse-proxy-using-forefront-tmg-2010-step-by-step/
For reverse proxy as name suggest, orgininating traffic will be from external and destination will be internal.
LikeLike
Thanks for your reply Raihan.
Regards,
Bruno B.
LikeLike
Hi Raihan,
I have a Forefront TMG set up in a 3-leg perimeter with 4 nic cards, configured as follows:
Internet
|
TMG — DMZ
— Perimeter
|
LAN
In the DMZ I have published an SMTP server
In the Perimeter a private data line to an outsource service
I would like to place a new TMG as the Front-End and make the current TMG a Back-End server. How can I accomplish this so:
1. Be a gradual transition
2. Do I have to make the TMG FE server a member of the Domain?
3. Which segments in the BE TMG I need to move to the FE?
Thanks,
Mike
LikeLike
Backend TMG will be member of domain. Frontend in workgroup. your smtp server should be in internal network. for proper functionality you have transition the systems and firewall at the same. plan ahead and do it.
LikeLike
Hi Raihan,
Thanks, yes I will be deploying the TMG servers over a weekend to avoid any downtime and my plans are like you suggested the BE-TMG will be a domain member and FE-TMG will be in a workgroup.
Current TMG Server: 3-leg with 4 NICs >>> External, Internal and 2 perimeter networks.
The problem or doubt that I have is where to place the current 3-leg TMG, can I make this server the BE-TMG and leave the perimeter networks as they are? Or would I have to remove the perimeter (2 NICs) and place it on the FE-TMG?
If I have to move the perimeter network (the 2 NICs) to the FE-TMG, because of hardware considerations my only option would be to remove the current TMG Server from the domain and rename the server before making it a FE-TMG. This would cause as you can imagine many issues with all the settings in place on this server (firewall rules, networks, etc.)
Please let me know what would be my options here,
Thanks,
Mike
LikeLike
Hello. Very good arcticle. But I have one question. Why perimeter network must have only public ip address range? Is it possible to use special private (not the same as internal corporate network) ip range for perimeter network? could you help me with this question?
thank you
LikeLike
depending on your network topology and infrastructure. yes you could have private ip
LikeLike
we are using IAS 2006 server for our Local Area Network, for URL filtering and VPN sharing, we used two Lan Adapters in our ISA2006 server, one is for ADSL (internet) and another one is Lan switch.also we have local win 2003 domain controller.
Now we planing to install Forefront TMG 2010 server in our Local network for URL filtering and VPN share, which operating system required for us? and which TMG server is suitable ? and we need any Domain control for this?. How to install Please guide me as soon as possible.Thanks for your replay.
Existing connection is “INTERNET -> ISA SERVER 2006 -> LAN SWITCH”
LikeLike
If you have bought enterprise version you can install back to back firewall using two TMG server. However if you have 1 TMG license than you can use Edge Firewall Topology.
Depending on your topology if internal users wants authentication than yes tmg can be member of domain.
use Windows Server 2008 Server
TMG 2010 Sp2
Here is guide http://microsoftguru.com.au/2010/03/08/forefront-tmg-2010-how-to-install-and-configure-forefront-tmg-2010-step-by-step/
LikeLike
which Forefront TMG network topology we have to install ? Thank you
LikeLike
I am Waiting for you replay Raihan Al-Beruni -Bai
LikeLike
Hi Raihan!!
Please help me !!! I’ve got problem with TMG. The problem is : “Cannot retrieve data from firewall”
how can i resolve that problem
LikeLike
what sort of data you cannot retrive? is it logs you are talking. check whether you have configured a logs?
LikeLike
Hi Raihan,
We currently are testing TMG2010 as a back end firewall with another appliance based firewall as the front end. do you have any information around this kind of a configuration?
Thanks for the assistance and guidance.
LikeLike
Hi Raihan,
We currently are testing TMG2010 as a back end firewall with another appliance based firewall as the front end. do you have any information around this kind of a configuration?
Thanks for the assistance and guidance.
LikeLike
Configure front end appliance as Edge Firewall & Backup TMG as Edge Firewall. Thats all. Add internal IP range into internal network of front end appliance/firewall to avoid spoofing. Publish firewall rules in backend and frontend. thats all you have to do
LikeLike
hi rehan i need ur help bro i read ur article it is really good but i m facing some problem…………
i installed tmg server with 3 machine one is domain ip=192.100 other is dmz ip=172.16.0.100 and one is tmg in tmg i have 3 lan card public,inside,dmz internet is properly working on domain i want to ping dmz to dc and dc to dmz its not giving response request time out,bro but tmg ping dmz what i do ?????? i also want to enable internet on dmz ???????????? need help
LikeLike
just create a firewall rule allowing ping to and from DMZ. not a best practice though
LikeLike